The Best Enterprise Risk Management Software
Get the best software for your business. Compare product reviews, pricing below.
Enterprise risk management (ERM) is the identification and assessment of common and critical risks which could cause delays or cancellations of regular business processes.
What is Enterprise Risk Management (ERM) Software?
Enterprise risk management software (also known as ERM software) is a specialized type of risk management software, a subset of BI tools, to help large-scale enterprises identify potential risks and weigh them against business opportunities.
Sometimes called risk management information systems (RMIS), it is designed to address growing technological threats like DNS and DDoS attacks which can take entire companies offline.
Due to the expanded scope of ERM, this software is primarily used by financial analysts and project managers at:
- Banking institutions
- Retailers
- Insurance companies
- Healthcare facilities
ERM software keeps these businesses operating as safely and successfully as possible. Identify key risks to your business objectives and prevent or prepare for them with risk management processes established by an enterprise risk management system.
Note: ERM should not be confused with enterprise resource management, which is more popularly known as enterprise resource planning (ERP).
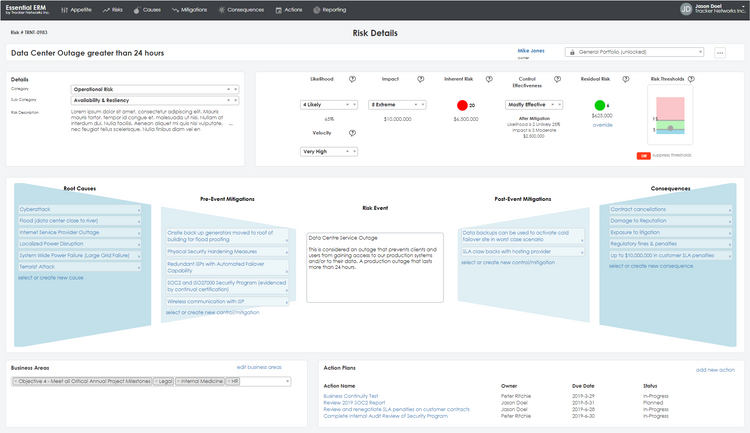
Features of ERM Software
- Risk analysis forecasting: Determine the possible costs associated with various risks along your business lifecycle and prepare your budget for handling these worst-case scenarios
- Predictive analytics: Use historical and real-time data to create custom business models to prepare for the unknown
- Incident response management: Create and implement plans to mitigate damage from incidents like power outages, cyber attacks, supply shortages, and more
- IT governance and cyber security: Set up secure data networks to prevent DNS and DDoS attacks
- Alerts and notifications: Receive automated alerts for real-time updates on projects during risk scenarios; send notifications to employees or customers when accidental outages or scheduled service interruptions occur
- Auditing: Save and review historical risk data related to past incidents in order to continually assess new risks and potential response tactics
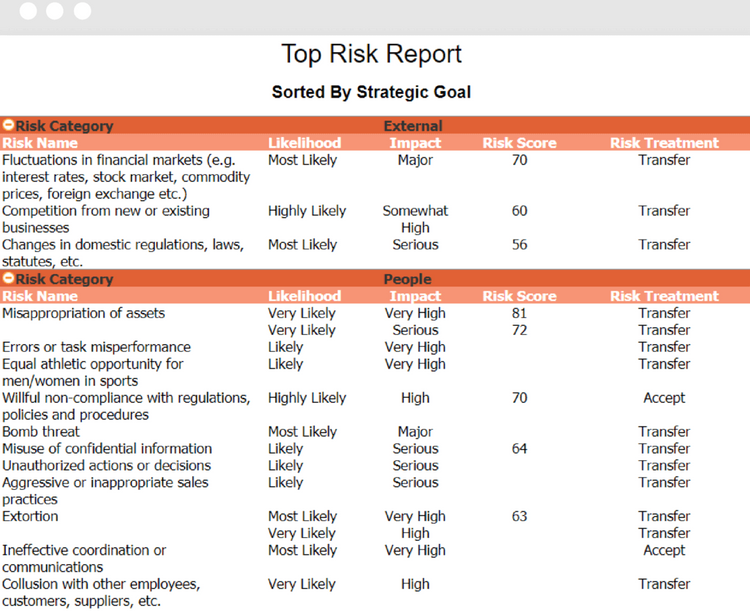
ERM Software Benefits
By improving your risk management practices, an ERM platform can help your company:
Prepare for Incidents, Accidents, and Attacks
The main benefit of ERM software is protecting and preparing your company from all types of disasters. The ERM process first identifies key risks based on your industry, operating territories, competition, and more.
This customizable risk assessment lets you improve your management system by knowing industry-specific problems. For example, distributed denial-of-service (DDoS) attacks are targeted attempts to interrupt web services. If you operate an eCommerce business, you need your website to stay up and running at all costs. An ERM provides additional cyber security measures for defending your domain from these attacks.
In the event a risk becomes a reality, ERM platforms provide incident response tools. Planning out your incident response tactics ahead of time means you can quickly implement these measures as soon as disaster strikes. By preventing service delays, you can reduce potential losses. In the case of a technological attack on an eCommerce website, an incident response may include switching to a backup server to prevent service interruptions to customers.
Improve Business Operations
Identifying risk has another benefit for your company: eliminating inefficient practices which lead to operational risk. An ERM program includes tools for spotting which competitive conditions in your industry may lead to reduced market appetite for specific goods and services.
For example, road construction near your warehouse may lead to shipping delays. You can calculate the effects of these delays in order to prioritize outgoing shipments. Once the construction is over, you can review these risk mitigation changes to see if they are worth keeping to optimize your services going forward.
Plan for Service Interruptions
In turn, knowing all possible risks and planning ahead helps you maintain customer satisfaction. Using automated notifications from an ERM software can alert your customers to planned outages or interruptions well in advance.
There are many ways you can use notifications to improve your business communications. Shipments being delayed? Send an alert so your partners know ahead of time. Power outage? Call in your incident response team with a push notification.
Remain Compliant with Changing Laws
Compliance management is another valuable tool provided by ERM. Regulatory agencies and governments are always changing laws to promote safer working conditions around the world. Avoid lawsuits, fines, and penalties via regulatory compliance managed through an ERM platform. A governance, risk, and compliance (GRC) application can track changing laws to ensure you remain compliant in every territory.
In the United States, information systems are protected by a risk framework or risk management framework (RMF) with six steps:
- Categorize
- Select
- Implement
- Assess
- Authorize
- Monitor
An ERM can help you establish these steps for your own network security.
Improve Credit and Insurance Rates
Safe businesses enjoy more financial rewards than their riskier counterparts. Unanticipated supply chain interruptions, say from a worker shortage, can cause you to miss out on sales. Employees injured on the job are entitled to expensive worker’s compensation. All of these unaccounted for risks can quickly add up. Instead of paying medical bills from preventable accidents or losing out on sales, use risk management tools to better prepare for all the possibilities and avoid these big payments.
Additionally, assessing your risks with an ERM can reduce your insurance rates and improve your credit ratings. Incident management plans demonstrate your company’s adherence to risk reduction practices.
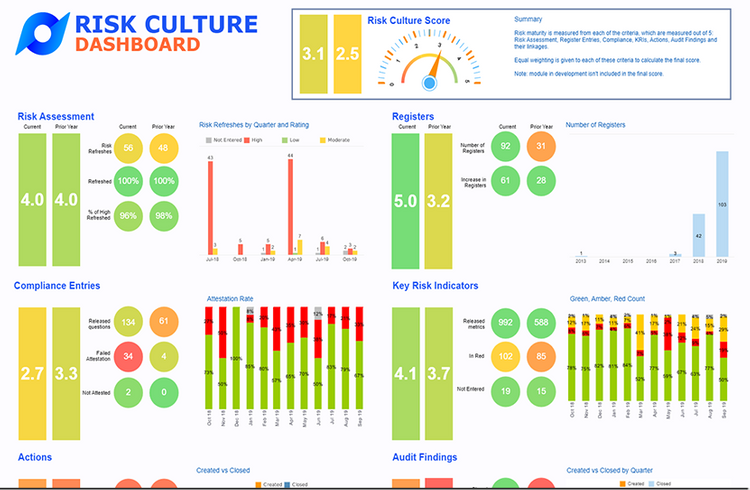
How is ERM Different from Risk Management?
Both ERM and risk management solutions are made to protect businesses from threats by identifying, quantifying, and minimizing risky situations. However, ERM is a specific type of risk software intended for larger corporations within the fields of finance, healthcare, retail, and insurance. A general risk management solution is more appropriate for all other industries. However, a smaller healthcare facility could use a risk management software while a larger company may benefit from an ERM.
There are also specific solutions for energy trading risk management (ETRM). This type of software is made for risks associated with the trade of assets on financial markets.

