The Best POS Systems
We’ve reviewed the top POS software to help single and multi-site retailers and restaurants process payments, manage inventory, and improve customer satisfaction.
- Automated purchase order creation
- Built-in SEO tools for online stores
- Fully integrated inventory management
- Multiple users have praised customer support
- Supports multiple locations
- Industry-specific POS software made for LBM business needs.
- Features mobile connectivity and special-order handling.
- Offers barcode support
Point of sale (POS) systems process customer transactions, accept payments, issue receipts, and handle back-office processes for your retail environment. We’ve compiled our list of the best POS systems for your small business based on our review methodology.
- Lightspeed Retail: Best Overall
- KORONA POS: Most Flexible
- RockSolid MAX: Best for Hardware Stores
- TouchBistro: Best for Restaurants
- Clover POS: Best for Multi-Site Retailers
- Square: Best for Startups
- The General Store: Best On-Premise Option
- J3 POS: Best for Specialty Retailers
- Shopify POS: Best for QuickBooks Users
- eHopper: Most Affordable
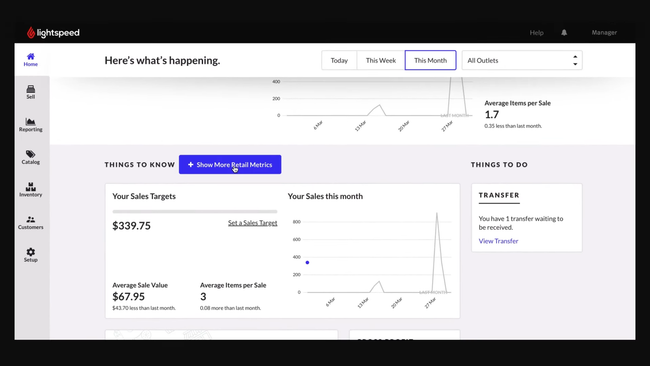
Lightspeed Retail - Best Overall
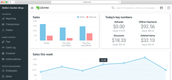
Lightspeed Retail is a point of sale system with strong omnichannel capabilities and inventory management tools. We like that the system integrates with eCommerce platforms like Amazon and Squarespace, tracking inventory across online sales and brick-and-mortar stores.
Additionally, Lightspeed’s inventory management allows you to set automated reorder points, manage purchase orders, and add product variations. The software makes managing different sizes, colors, or materials easy and bundles products for promotions or special sales. In its restaurant edition, you can even track inventory on the ingredient level for more precision.
Lightspeed integrates with accounting software such as QuickBooks Online. However, their basic plan starts at $89/month annually for one location, making it one of the more expensive options on the market. Still, it’s worth the price for larger retailers and restaurants needing a comprehensive system.
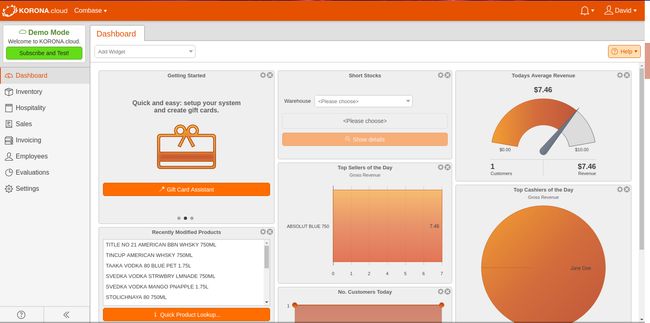
KORONA POS - Most Flexible
KORONA POS is a payment processor-agnostic platform, meaning you can use any service you want. This can save you hundreds or even thousands per year in processing fees, especially if you have a high monthly transaction volume. That’s because most POS systems like Lightspeed Retail and Square force you to use their own processor, which usually has flat fees. With KORONA, you can shop for variable or lower rates and switch at any time.
Additionally, KORONA has an open API that makes integrating CRM tools, loyalty programs, and accounting systems much easier. They provide flexible payment options for POS hardware like receipt printers and cash drawers, allowing you to lease or purchase them in installments. If your existing hardware is compatible, it can also be integrated with KORONA POS.
KORONA’s core plan costs $59/month. While cost-effective, it’s missing some vital features like stock management, real-time tracking, and customer management. To get these, you’ll need to upgrade to KORONA POS Retail at $69/month, which isn’t too big of a price jump.
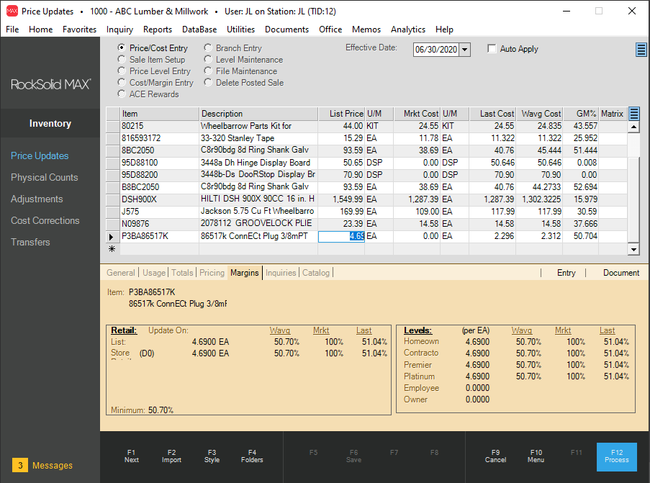
RockSolid MAX - Best for Hardware Stores
RockSolid MAX is a top option for small to medium-sized hardware stores. The software integrates smoothly with wholesalers like Ace and True Value, enhancing stock accuracy and special order handling.
We like that RockSolid MAX supports multi-location businesses, allowing you to track inventory across stores. The software also suggests optimal order quantities during purchase order entry, ensuring you always have the necessary stock.
Overall, the system is a good option for managing sales, purchasing, and data analytics with up to 10 concurrent users. While RockSolid MAX has a variety of built-in reports, you’ll need some expertise in Crystal Reports to customize them. Additionally, pricing requires a consultation call.
TouchBistro - Best for Restaurants
TouchBistro is an iPad-based restaurant POS system that handles pending vendor checks, lets your waitstaff send orders, and processes customer payments. It accepts many payment methods, including gift cards, digital wallets, and credit cards.
TouchBistro’s tableside service (such as order placing) can help turn tables faster. It also provides suggestions to servers to pass on to the customer. A kitchen display system for the back of the house will immediately update the cooks with what needs to be completed–including substitutions–and in what order.
That said, our research shows TouchBistro has fairly limited integration options compared to alternatives like Lightspeed. It’s also exclusively compatible with iPads. This can increase your initial setup costs if you use other types of tablets or operating systems.
Clover POS - Best for Multi-Site Retailers
Clover POS provides a reduced barrier to entry with various propriety hardware options. These include everything from mobile payment devices like Clover Go to full POS systems like Clover Station. These allow retail owners managing multiple locations to easily add additional hardware that makes sense for the specific location. For example, a large flagship store will be more apt to use the Clover Station, while a small boutique location can use the Clover Flex or Go.
We like that the software offers functionalities for online ordering and sales, invoicing, and payment processing. Customers can pay with credit cards, debit cards, and contactless options like Apple Pay and Google Pay. Because the system is cloud-based, you can view sales and order history for all stores.
However, replacing your existing hardware for Clover’s specialized equipment can lead to higher upfront costs. If you switch providers, you can’t reprogram Clover’s equipment for use with other systems. Additionally, Clover POS subscriptions are non-cancelable and ineligible for refunds, which has led to some user frustrations.
Square - Best for Startups
Square provides a one-stop shop for startups looking to get up and running fast. It offers more affordable hardware options than other competitors like Clover POS, allowing for a lower initial investment. Whether it’s iPad stands, mobile terminals, or simple card readers, you can bundle them with the software so you don’t have to shop for third-party equipment. It even lets you repurpose existing devices, like kitchen and receipt printers, routers, and cash drawers, so you’re not forced to use their hardware if you already have equipment.
Additionally, we appreciate that Square POS has a free plan with no setup costs. However, there’s a standard processing fee of 2.6% + 10 cents for in-person credit and debit card transactions. Still, this is pretty standard in the POS market, with other vendors like Lightspeed Retail having the same rates.
Unfortunately, Square isn’t compatible with Windows devices, so you’ll need an iPad or iPhone to get started. And though it offers restaurant plans, full-service sit-down establishments with complex menus might need software with more advanced features, like TouchBistro.
The General Store - Best On-Premise Option
The General Store is best for small retailers that don’t want a cloud-based system. The software provides CRM and inventory management for a one-time purchase fee, avoiding the ongoing costs of subscription-based pricing. We also like that The General Store supports several payment processing terminals, barcode scanners, and cash drawers.
The software’s inventory control feature supports up to 10 different pricing levels, plus multi-unit pricing. It also enables sales tracking for both cash and credit customers. Along with tools like a built-in time clock, The General Store helps manage employees, monitor sales by period, and track commissions.
The General Store is available for a one-time purchase of $695 for a single user, plus an annual technical support fee of $600. However, some reviewers have expressed dissatisfaction with the support cost and the dated-looking interface.
J3 POS - Best for Specialty Retailers
J3 POS offers a highly flexible software catering to more niche retail stores. For example, an organic grocery store can tweak the modules to include an integrated scale system and flexible pricing structures. Additionally, the software scales quickly, making it a good fit for boutiques and multi-location retailers.
J3 POS is customizable with options like mobile checkout and loyalty programs, making it ideal for expanding businesses that manage multiple store locations. Additionally, the system integrates with QuickBooks Online and Desktop for instant updates between sales, inventory, and financial records.
However, J3 POS does not publicly list its pricing. You’ll need to request a personalized quote to find out what you’ll pay.
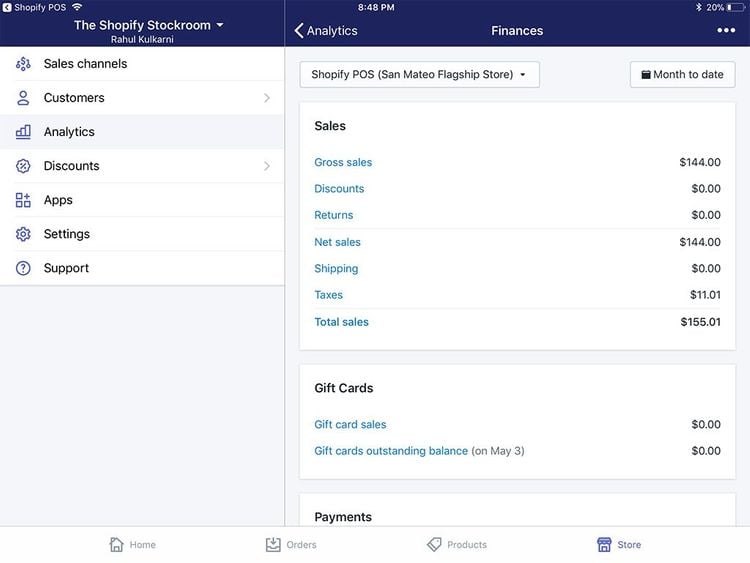
Shopify POS - Best for QuickBooks Users
Shopify POS is an effective alternative for businesses transitioning from QuickBooks POS, which Intuit discontinued in 2023. Shopify offers a migration tool, 24/7 support, and premium onboarding services, easing the shift for former QuickBooks POS users.
Additionally, we like that Shopify integrates with both QuickBooks Online and QuickBooks Desktop. However, the sync frequency with QuickBooks Desktop through the connector app has been adjusted from every 5 minutes to once daily at a user-specified time. This can help reduce the system’s workload and potential errors due to constant updating. But this also means you won’t see real-time updates to financial data unless you use the manual sync option.
eHopper - Most Affordable
eHopper is best for small companies due to its free credit card processing through a cash discount or credit surcharge program. You can agree to either add a surcharge to credit card sales or give a discount for cash sales, saving your small business from steep processing fees.
You can access the platform on both Android and iOS tablets, mobile devices, or Windows and Mac computers via a web browser. eHopper also offers an “all-in-one” POS with a 14-inch touchscreen register.
Their paid options start at just $10/month annually for the Essential Plus plan, making it affordable for beginners. You can also use the Free POS plan if you’re a US-based micro-business. However, card processing is only available through eHopper, so you can’t use other providers.
What Is A Point of Sale (POS) System?
A point of sale system handles the payment collection, receipting, and inventory updating involved with a retail sale in real time at the point of purchase. A POS system will scan items at checkout, calculate the amount owed, and prepare an invoice that customers can immediately pay via credit card, cash, or check.
Some POS systems are all-inclusive and include bundled hardware, such as an iPad or a fully operating cash register, barcode scanner, and credit card swiper. Other POS software options can operate as web-based software via a browser–allowing you to use whatever computer or mobile device you are familiar with.
Critical business benefits enabled by point of sale systems include:
- More accurate and timely retail accounting based on the ability to integrate POS functions with core accounting applications
- Improved customer satisfaction based on rapid checkout experiences
- Increased sales revenues supported by more effective promotions management and the delivery of cross-sell/upsell recommendations to retail staff
- Reduced stock management costs as a result of automated inventory count updates following customer transactions
Key Features
- Payment processing: Set up a merchant account and accept various customer payment methods. Support payments in multiple formats, including cash, credit card, check, and gift card
- Refunds and return management: Evaluate item conditions, restocking, and issuing refunds/credits
- Receipting: Documents transaction details, often in a variety of receipt formats
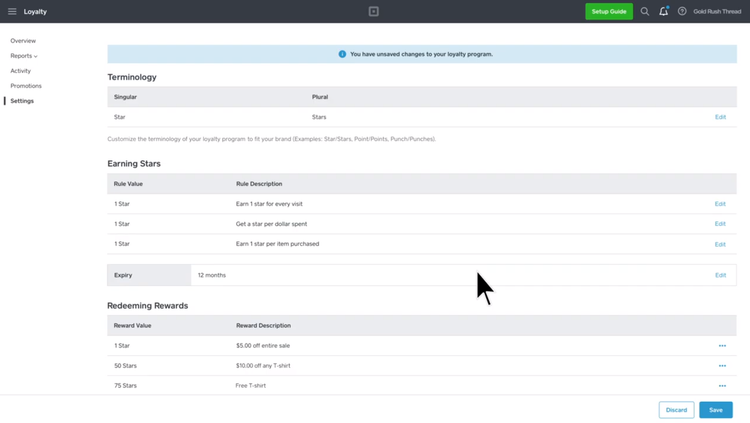
- Customer loyalty/rewards programs: Allow customers to accrue benefits or store credit based on order histories or other factors; can be used to improve customer retention
- Promotions management: Manage discount deductions item/customer eligibility checks and with automated cost calculation
- Item look-up: Allow cashiers to check on item availability from a POS terminal
- Customer database: Track contact information, buying histories, and other factors
- On-account sales: Allow customers to receive items immediately and make payment on an issued invoice at a later date
- Age verification: Verify age for items such as alcohol and tobacco
- Gratuities management: Allow customers to leave tips and provide support for gratuity calculation and reporting on compensation distribution
- Online payment integration: Enables the use of services such as a PayPal, Venmo, and Apple Pay
Primary Benefits
Point of sale represents the area where retail businesses conduct their data entry. From moving customers through the checkout line to automatically integrating with back-end financial management systems, point of sale systems provide tools to improve productivity.
Point of sale software opens up a host of other major business opportunities:
- Real-time access to accurate inventory counts
- Automatic integration with accounting software
- On-the-spot upsell recommendations
- Improved markdown and promotions management
- Tighter controls for return authorizations
- Customer info tracking for ongoing marketing
- Product sales trending
Improve Your Investment Returns With POS Systems
Three big factors have contributed to lowering costs and improving ROI rates for investments in POS systems:
- Cloud-based, SaaS options mean retailers can spread costs over time rather than make a significant capital expenditure on a new system.
- An increase in the number of POS providers developing software creates price competition while allowing for tighter targeting of niche industry requirements–limiting the need for expensive customization.
- Mobile apps have turned phones into portable payment kiosks, minimizing hardware requirements while enabling retailers to take the transaction from the counter to the sales floor and beyond.
Automate the Retail Counter Experience With POS Systems
Accurately inputting items sold, quantities, and prices can be automated in several different ways. Many point of sale applications allow for barcode scanners to transmit information about the item being purchased. Whether the information is gathered through touch screens, bar codes, or manual input of item codes, POS systems will associate the item and quantity input with a per-unit price.
Point of sale systems are also responsible for summing the total of all items and providing a balance due figure. Errors are more likely with manually calculated balances than those derived automatically by software. Also, the ability to create line item records for every item sold is a first step in preventing fraud and theft.
Track Buying Trends With A Point of Sale System
An often-overlooked capability of a point of sale system is intelligent software’s ability to promote increased sales volumes. The POS offers a tremendous opportunity to get to know your customers and appeal to their needs.
Detailed sales histories let you see firsthand what your hottest sellers are and which products are not moving as fast as you’d like. Understanding the buying trends of individual customers further helps target sales opportunities–provided the information is shared with the right employees at the right time.
Access Key Point of Sale Reports
Point of sale systems capture data critical to making solid business decisions. POS systems can be integrated with inventory software to deduct items from inventory as they are sold. Understanding precise inventory stocks and the rate of sales on products allows retailers to make good decisions on when to re-order items. Ordering stock wisely means ensuring availability without tying up cash in overhead expenses.
Enable Multiple Payment Options
The cash-only retail business is quickly fading into obscurity. Today’s consumers expect uniform access to the payment method of their choosing. Point of sale systems help to accommodate this business reality.
POS system modules allow credit card processing and are built to easily receive input from credit card swipers. While credit and debit options have reduced the number of checks being written, many customers still expect the option. Payment by check has historically offered an opportunity for fraud and lost revenues, but modern point of sale systems have introduced security tools to help minimize this possibility.
Many POS applications can integrate with check reader hardware and check verification services. Of course, virtually all point of sale systems require the ability to support cash transactions. Tight integration between the point of sale software and the cash drawer is a must.

Hardware Integration
Most point of sale experts recommend choosing software and basing the decision on what hardware to use on the software system, rather than vice versa. The basic reason for this is that the software provides the intelligence in the system and will have more specific requirements about which hardware devices can be integrated.
Typical hardware needs for POS set-ups include:
- Credit-card swipers
- Computer terminals
- Monitors
- Bar-code scanners
- Receipt printers
- Touchscreens
- Computer peripherals such as keyboards and mice
- Cash-drawers